Zero-Day Vulnerabilities: Understanding and Mitigating the Risk
Zero-day vulnerabilities are among the most dangerous security threats faced by organizations today. These vulnerabilities refer to unknown software flaws that are exploited by attackers before developers have a chance to issue a patch or fix. The term "zero-day" signifies that the developers have "zero days" to resolve the issue.
How Can Zero-Day Vulnerabilities Affect You?
Zero-day vulnerabilities pose a severe threat to organizations and individuals alike. Because these flaws are unknown to the software vendor, attackers have a significant advantage in launching exploits that can bypass traditional security measures. Notable incidents include the Stuxnet worm and the 2021 Microsoft Exchange Server vulnerabilities.
Organizations relying on proprietary or widely-used third-party software are particularly at risk. Successful exploitation can lead to data breaches, unauthorized system access, financial losses, and severe reputational damage.
Understanding Zero-Day Vulnerabilities
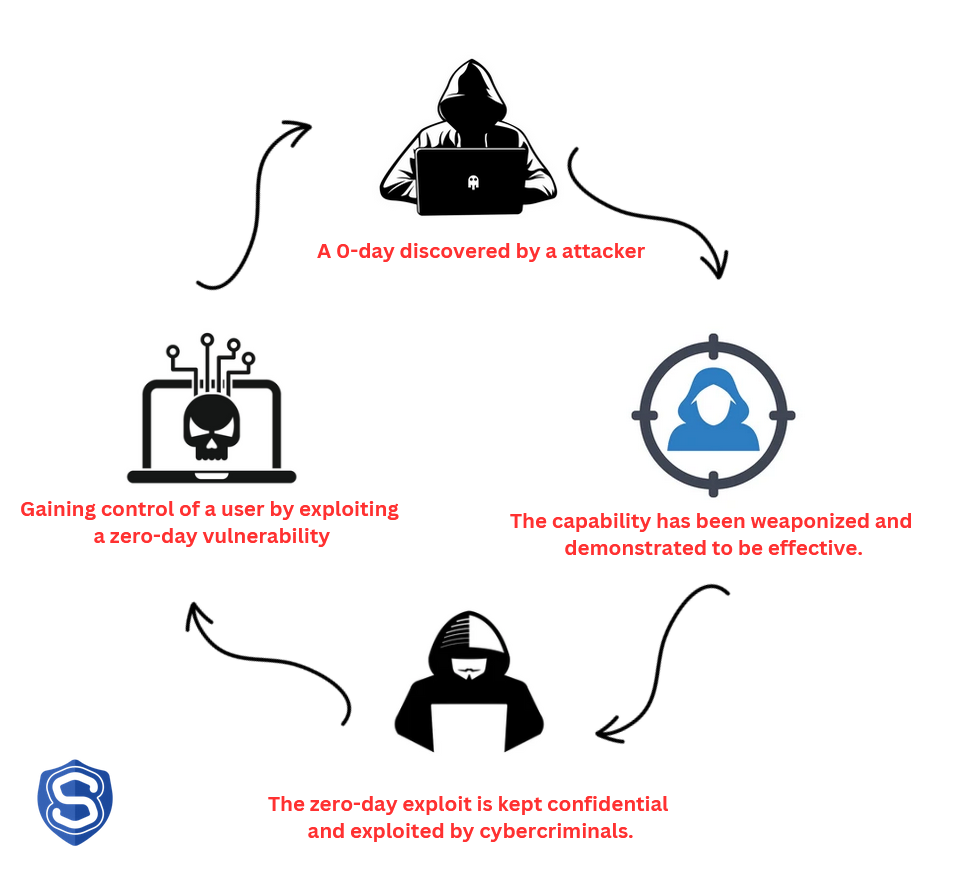
These vulnerabilities typically emerge when developers inadvertently introduce security flaws during software development. Attackers discover and exploit these weaknesses before the software vendor becomes aware of them. Zero-day attacks can take the form of malware infections, data exfiltration, or unauthorized access to systems.
Mitigating Zero-Day Vulnerabilities
While completely eliminating the risk of zero-day attacks is challenging, adopting best practices can significantly reduce exposure:
Apply Defense-in-Depth Strategies: Implement multiple layers of security controls to mitigate risks.
Use Threat Intelligence Feeds: Stay updated on emerging threats and indicators of compromise.
Regularly Update and Patch Software: Keep all applications and operating systems up-to-date to minimize vulnerabilities.
Implement Network Segmentation: Isolate critical assets to prevent lateral movement in case of an attack.
Monitor System Behavior: Continuously analyze system logs and network activity to detect anomalies.
Conduct Security Audits: Perform regular vulnerability assessments and penetration testing.

