Preventing Dependency Confusion Attacks
Software libraries play a crucial role in development, enabling engineers to build applications efficiently. Most programming languages feature package managers that handle installation and updates. However, this convenience also introduces risks, such as dependency confusion attacks.
Dependency confusion occurs when a package manager mistakenly installs an unintended public package instead of a private one, potentially exposing sensitive information or introducing malicious code. It is vital for developers and organizations to understand this risk and implement defenses.
How Can Dependency Confusion Affect You?
In 2021, security researcher Alex Birsan exposed this attack vector by breaching companies like Apple, Microsoft, and Tesla. Again, in December 2022, PyTorch users experienced a targeted attack on their nightly builds, demonstrating that dependency confusion remains an active threat.
Organizations maintaining private code repositories should be cautious. If a public package shares the same name as an internal one, and the package manager prioritizes public sources, malicious code could be installed inadvertently. As reliance on third-party dependencies grows, so does this risk.
Understanding Dependency Confusion Attacks
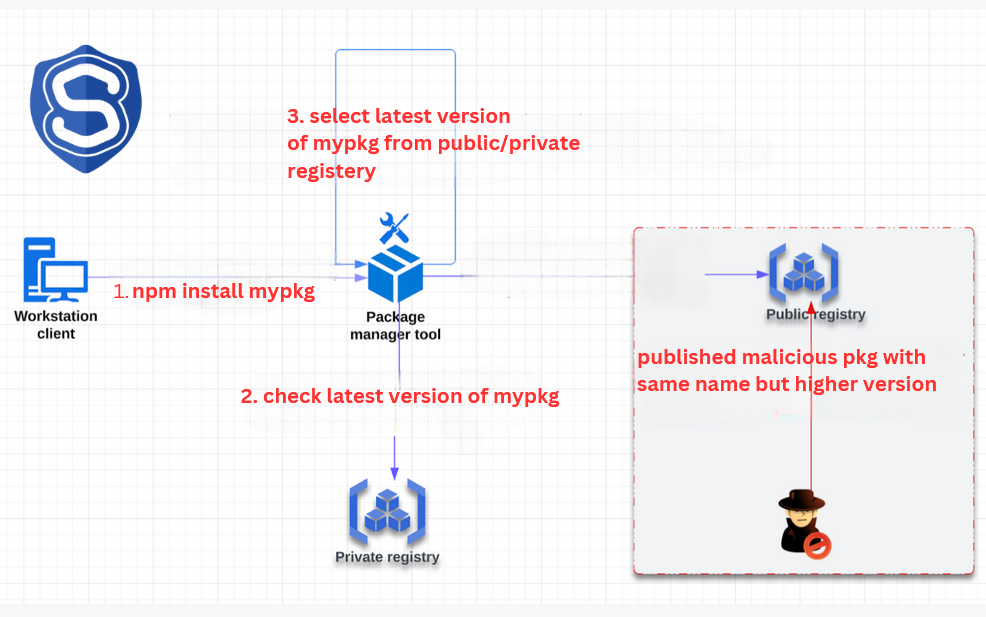
These attacks exploit the versioning system of package managers. An attacker uploads a malicious package with a higher version number to a public repository. When a developer installs dependencies without specifying a source, the package manager may select the higher version from the public registry, leading to potential security compromises.
Mitigating Dependency Confusion Attacks
While no single solution eliminates supply chain risks, best practices can reduce exposure:
Verify Dependencies: Use digital signatures or checksums to ensure package authenticity before installation.
Use Internal Package Registries: Maintain private repositories to prevent accidental installation of public packages with the same name.
Enforce Versioning and Namespacing: Specify exact package versions and use unique namespaces to avoid confusion.
Safelist Dependencies: Only allow installations from pre-approved, trusted sources.
Monitor Package Usage: Continuously track dependencies to detect unauthorized or suspicious packages.
Educate Your Team: Train developers and security teams on recognizing and mitigating dependency confusion threats.

