Understanding and Preventing Data Breaches
In today’s digital landscape, data breaches are a persistent threat to organizations of all sizes. These breaches occur when sensitive, protected, or confidential data is accessed, disclosed, or stolen by unauthorized individuals. Businesses and individuals alike must stay vigilant and adopt robust security measures to safeguard their information.
How Can Data Breaches Affect You?
Data breaches can have far-reaching consequences, including financial losses, legal repercussions, reputational damage, and identity theft. Major incidents, such as the 2017 Equifax breach and the 2021 Facebook data leak, exposed the personal information of millions of users, highlighting the need for stronger cybersecurity practices.
Organizations that store customer data, financial information, or proprietary assets are particularly at risk. Failure to implement proper security measures can lead to devastating consequences, including compliance penalties and loss of customer trust.
Understanding Data Breaches
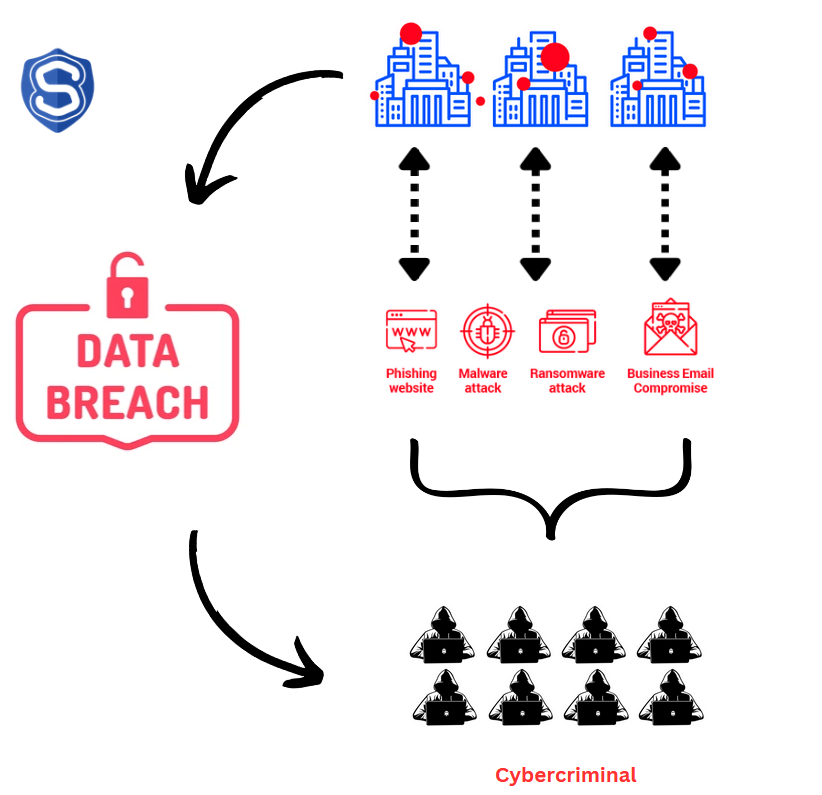
Data breaches typically occur through various attack vectors, including phishing attacks, which trick victims into revealing sensitive information through fraudulent emails or websites; malware infections, where malicious software is deployed to infiltrate and extract data from systems; exploitation of vulnerabilities by taking advantage of unpatched security flaws in applications or networks; and insider threats, involving unauthorized actions by employees or partners with access to sensitive data.
Preventing Data Breaches
While no organization is entirely immune, best practices can significantly reduce the likelihood of data breaches:
Implement Strong Authentication: Use multi-factor authentication (MFA) to protect user accounts.
Regularly Patch Systems: Ensure all applications and operating systems are updated with the latest security patches.
Encrypt Sensitive Data: Protect data at rest and in transit using robust encryption methods.
Conduct Security Awareness Training: Educate employees on recognizing and avoiding security threats.
Monitor Network Traffic: Continuously analyze network activity to detect and respond to suspicious behavior.
Maintain Incident Response Plans: Develop and regularly test response strategies for potential data breaches.

